How To Handle Your Company’s Sensitive Data
Both large and small businesses are attractive targets for hackers because they store sensitive data — like personal and financial information — about clients, employees, and suppliers. This information can be used for fraud and identity theft, among other illegal purposes, and the cost of protecting this data is increasing every year.
Damages from data loss or disclosure can be devastating for companies. It can harm their reputation, destroy customer trust, and lead to financial and legal consequences. Businesses need to stay alert and make sure their data is secure. In this article, you will learn about the sensitive data you are likely to be responsible for through your business and how best to protect it.
What Is Sensitive Data?
Sensitive data includes personal, financial, and business information about a company’s customers, employees, or business partners. It is valuable information that needs to be protected against unauthorized access and disclosure. The primary sensitive information your business is likely to handle is:
- Personal data: Customer information that can uniquely identify an individual, like a user’s address, phone number, or birthdate, or more delicate information like health records.
- Financial data: Includes credit card and bank information, and Social Security numbers.
- Business data: Businesses hold various types of information that could cause them damage if stolen or released. Sensitive business data includes trade-specific secrets, intellectual property, financial and accounting information, and supplier confidential information.
Personal and financial data, also known as personally identifiable information (PII), can be combined and used to impersonate a user to commit fraud or identity theft. Its usage and protection is therefore heavily regulated.
Protecting the sensitive data you hold requires careful planning and implementation using the right tools. You must know what data you hold, how it is being used (and that it is being used within the legal justification for which it was collected), and where it is located.
Regulations on Sensitive Data
To enforce data protection for the public, government and industry regulations define how you can collect PII and how you can use it. Below are some examples of the regulations that are likely to cover the data you handle.
General Data Protection Regulation (GDPR)
The General Data Protection Regulation (GDPR) determines when and how personal data may be used, stored, deleted, transferred, and processed, as well as how to protect it. The GDPR applies to every company that handles the data of EU citizens. The rules are complicated, and the fines for violations are strict.
The GDPR’s definition of personal data encompasses any information that directly or indirectly identifies a person and can lead to identity theft. This includes names, emails, IP addresses, phone numbers, and location data. The law also specifies more sensitive information that businesses must treat with extreme care, such as racial origin, political views, religious beliefs, biometric data, and sexual orientation.
With the GDPR, organizations must inform users beforehand what information is collected and how it will be used. Users can reject this when the data is intended for “profiling” or direct marketing purposes, and they can demand the correction of false or incomplete information, or request the deletion of their data in its entirety.
California Consumer Privacy Act (CCPA)
The California Consumer Privacy Act (CCPA) is a data privacy law designed to protect California consumers’ rights. As of January 1, 2020, businesses are obligated to inform consumers how they handle their data.
The CCPA and the GDPR have similar definitions of personal information. According to the CCPA, any information that can lead to the direct or indirect identification of a specific consumer or household is considered personal.
The CCPA also covers data from online activities like your search and browsing history, purchase history, cookies, or other tracking techniques that can be linked to specific individuals. Similarly, biometric and geolocation data as well as characteristics like race, religion, age, or sexual orientation and any information that isn’t de-identified is considered personal under the CCPA, and businesses are obligated to protect it.
Health Insurance Portability and Accountability Act (HIPAA)
The Health Insurance Portability and Accountability Act (HIPAA) is a US law designed to set privacy standards for protecting medical records and other patient information provided to doctors, hospitals, healthcare providers, and all their business associates.
HIPAA specifies technical and organizational measures that must be implemented to safeguard protected health information (PHI) and signals the obligation of healthcare providers to establish and comply with strict data security protocols when handling this data.
HIPAA differs from other regulations because it doesn’t require a patient’s consent to use their data. Healthcare providers are free to process this information as long as it’s handled in compliance with appropriate security measures. Under HIPAA the healthcare provider isn’t obligated to amend or delete a user's personal data. HIPAA also allows providers to disclose a “limited data set” to a marketing company without patient consent, as long as it doesn’t identify an individual directly.
Payment Card Industry Data Security Standard (PCI DSS)
The Payment Card Industry Data Security Standard (PCI DSS) is a set of standards, policies, procedures, and tools designed to protect a cardholder’s data.
PCI standards are developed and maintained by the PCI Security Standards Council (SSC). There are twelve basic requirements grouped into six categories that aim to create a secure global payment environment that protects businesses and consumers from security breaches and card data theft.
Application of PCI DSS is mandatory for every organization that stores, processes, or distributes card information. This includes financial institutions, point-of-sale (POS) payment providers, and businesses of any size.
According to the PCI standard, sensitive personal data includes the name of the cardholder, the card number, and the expiration date. It also includes authentication data like the card verification value (CVV) code, personal identification number (PIN), and information stored on a magnetic stripe or chip.
PCI DSS compliance requires continuous effort due to evolving threats. You should be aware of any updates or modifications.
How to Manage Sensitive Data
Legal compliance should not be the only motivation for you to secure your sensitive data. Doing the bare minimum is not enough, and you should consider the following measures when deciding on your data security strategies.
Identifying the regulations you must comply with
The above regulations on sensitive data are not an exhaustive list, and the laws surrounding PII are regularly being updated. You must research the regulations you need to comply with based on the kinds of data you store and process, and stay up to date with any new or updated requirements.
You should be aware of the risks and obligations you should meet to ensure customer trust, and regularly review your data for any new potential risks or responsibilities.
Data Masking
Data masking obscures data in a way that makes it practically useless to unauthorized users. The most common example of this is the obscuring of all but the last four digits of a credit card number when it is displayed. Enough information is provided that you can confirm that the correct data is present, but the information provided is not enough to be of any use if unintentionally disclosed.
Data masking is categorized into static data masking (SDM) and dynamic data masking (DDM). SDM stores the real, unmasked, data in one database unaltered and the masked data in a separate database. DDM maintains only a single database containing unmasked data. When data is requested by parties who are not entitled to see the unmasked data, SDM will return data from the masked database, while DDM masks it in real time.
Data masking is a powerful security tool that has been mandated by all the major regulations mentioned earlier, while being inexpensive and technologically simple to implement.
When working with masked data, a good practice is to peer review the data to make sure everything is masked and that no production data is used in any non-production environments. Multiple masking techniques can be used to make the output more meaningful based on the context.
Controlling Access
Access control means the policies and technologies you implement to determine who has access to your data. In a well implemented data access control system, users should have access only to the data they need and nothing more. This is known as the principle of least privilege (PoLP) and can be implemented using role-based or attribute-based access control.
Keeping track of all devices connected to your systems and ensuring that they are not a security risk is also essential. With more people working from home, it has become common for them to access company resources from their personal devices, increasing the potential of data breach. Businesses should implement policies that restrict users to vetted devices, and enact technical measures such as remote workspaces and VPNs to ensure data is not accessed insecurely.
Encryption in transit and at rest
Data is considered “in transit” while it is being transferred over the web or a private network; for example, when you submit a form or upload files to the cloud. Data “at rest” is kept on any kind of persistent storage, such as the cloud, hard drives, or flash drives.
To prevent eavesdropping, data in transit should be encrypted by using encrypted network protocols such as SSL/TLS and HTTPS that use both symmetric and asymmetric encryption techniques.
To protect sensitive data at rest, you should implement an encryption solution that will allow only verified users with encryption keys to access it. Even if information is compromised, it is unreadable and therefore has no value to the attacker. Implementations of encryption for data storage include EBS encryption for AWS, Oracle Vault for Oracle Database, and BitLocker for Windows Server. Application-level encryption, if supported by your tools, is one of the best options for protecting sensitive data. At this level, data is secure regardless of its location, whether it’s stored on external devices, in databases, in applications, or in transit over a network.
Securing Your Network
There are several basic measures you should take to secure your network infrastructure and help prevent data breaches: protecting your network with a firewall, implementing a VPN for remote users, and keeping your software patched.
A firewall prevents access to your internal network resources. A firewall controls which services in your network are accessible to the outside world, blocks potential vectors for outside attack, and can be configured to flag or block suspicious outbound connections from your network to the internet.
A VPN is a secure connection over the internet that connects two or more private networks. VPN traffic is encrypted, and provides a secure way to access remote resources without having to expose public endpoints. VPNs were traditionally used to connect the networks of separate office locations, and have now become vital to enabling secure remote work.
Frequently updating your security/antivirus software, operating system, and web browser will help to protect against malware and hackers. You should ensure that your software is configured to enforce the automatic installation of security updates, and ensure that staff using their own devices install updates as soon as they become available.
Backing Up Data
Systematically backing up the data on all your devices is the most important step that you can take to avoid data loss. Back up your data regularly and store copies in three separate physical locations — including on site, in the cloud, and in a separate secure physical location. If your infrastructure is entirely cloud-based, store a backup of your data with a different cloud host, in case you lose access to your primary provider.
Backup strategies can protect businesses from software and hardware failures and data corruption from malicious software including ransomware. Backups are also a reliable way to recover deleted, overwritten, or destroyed files.
Regularly reviewing your data security apparatus
You should regularly review your security strategies and technologies for new vulnerabilities. You should audit and patch the software you use, and maintain detailed logs and monitor them for any signs of unauthorized data access or malicious activity.
If you identify any vulnerabilities or surreptitious data breaches, you must notify the affected parties and take measures to deny further access to sensitive data.
Preparing your staff to handle sensitive data
Poorly trained, negligent, and sometimes just plain unlucky staff are often the biggest vulnerability to your sensitive data. Training your staff in good security practices is a necessity if they are to handle, or have access to, any sensitive information. Your staff should adopt the following practices to help maintain the data security of your organization.
Being aware of information that should not be shared
It is vital to ensure that your data is correctly categorized, and access restricted to only those that require it, while ensuring those users are fully aware of the kind of data they are handling and their responsibilities toward protecting it.
Some data is intended to be shared — for example, product lists may be shared with customers. Those responsible for publishing or sharing information should be trained to check that no sensitive information is unintentionally included. If sensitive data does need to be shared, you should establish a legal basis and agreement to its usage prior to sharing.
Staff should be careful when providing information to others — even known parties. While it can be nice to be helpful, proffering information too willingly can be exploited by dishonest parties.
Detecting and reporting phishing attacks
Phishing is when hackers trick your employees into revealing information (like a bank account number), or performing an action (like granting access to your systems). The attempt may come as a phone call, SMS/instant message, or email. Some of these are obvious, like misspelled SMS messages asking for a money transfer, and some are more nefarious — complex attempts at impersonation aimed at extracting specific information.
Employees should be suspicious of any request for information, and check that the request is legitimate before fulfilling it.
Using secure communication channels and confirming identities
Your organization should provide secure communication channels to all staff to make phishing more difficult. This includes:
- Email hosted on a custom domain, secured with SPF and employing robust threat filtering
- Secure instant messaging like Microsoft Teams or Slack, with access restricted to accounts from your email domain
- Secure conferencing using Google Meet or Zoom, with attendance restricted to invited parties to prevent eavesdropping
A common phishing tactic for hackers looking to gain information on, and eventual access to, a network is to impersonate another employee, often using details gathered from public organization charts or LinkedIn. They may request seemingly benign information like email addresses, names, or phone numbers, that they will use to further impersonate organization members until they find a weakness to exploit.
If your staff receive a communication through a non-secure channel, or are suspicious that the person that they are talking to may be an impostor, they should have an alternative means of contacting the other party to confirm whether it is really them or not.
Enabling a culture of transparency
An educated employee is the first defensive measure against cyberattacks. However, no matter how savvy you are, mistakes happen. Make sure that, if a mistake is made that leads to a potential security incident, your staff are comfortable making the issue known so that the damage can be mitigated.
If your staff fear reprimand or punishment for an innocent mistake, they may try to cover it up. Time is a factor when responding to any data security incident, and any delay worsens its severity — giving attackers time to further time to cause harm. It will also leave you open to legal repercussions if you do not disclose data breaches and take appropriate measures to correct them.
How a customer data platform (CDP) helps you handle sensitive data
Attentive staff and privacy-aware data tools, combined with the best practices outlined above, will help ensure that your data is safe from loss and protected from unintended disclosure.
The technical data protection measures outlined in this article are supported by all major data warehouses and relational databases hosted on cloud or enterprise environments.
Your data security measures, however, shouldn’t just address who accesses your data and where it is stored, but must also consider where and how it is processed. Customer data platforms (CDPs) are a powerful tool that can assist in the handling of sensitive data in your business, and should both comply and assist with the implementation of your data security policies.
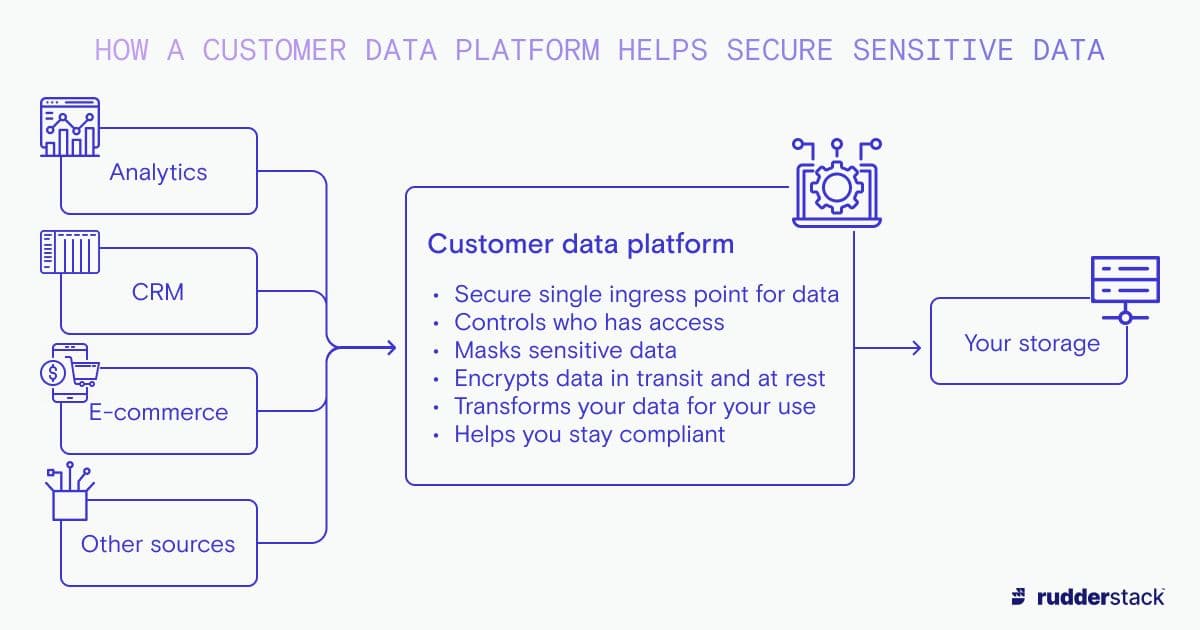
How a customer data platform helps secure sensitive data
The CDP you use to drive your customer data pipelines should allow you to securely ingest data from multiple sources, transform it (including masking sensitive data and flagging PII so that it can be properly handled), and then send it to secure storage in your data warehouse, relational database, or other storage solution — helping to protect it and making it readily available for future analysis and decision making.
Further reading
This article outlined the steps that you should take to secure the sensitive data that your business is responsible for. For more information on data security, take a look at the following Rudderstack Learning Center articles:
On this page