Data Protection Security Controls
What is data security?
Data security is the prevention of unauthorized access to or modification of your data. The widespread adoption of remote working gives employees greater flexibility and productivity; however, you must ensure you are adequately prepared for the increased risks to your company’s data security that comes with it.
This article explains the importance of implementing good data protection security controls, and the many different ways that a hacker can gain access to your data. It also details the security controls you should implement in order to follow best practices and ensure your business’s viability and reputation do not suffer damage from a costly data breach.
Why is it important to keep your data secure?
You have a responsibility to your customers to protect their data, especially sensitive personally identifiable information such as trade union membership or details of medical conditions. Allowing your customers’ sensitive data to be exposed can have devastating or life-changing effects for them, and can also cause significant damage to your reputation and brand.
Fixing issues after a data breach is expensive and sometimes impossible – once sensitive data has been leaked, it can’t be unleaked. This can lead to big fines from regulators who enforce compliance with laws such as GDPR, CCPA or LGPD, and financial compensation claims from your customers. All of this would be incredibly stressful for you and your team, and dealing with this major issue could lead to reduced productivity and increased employee turnover. Disasters like this damage both the reputation of a business and the business itself.
Common ways attackers gain access to your data
Hackers are inventive, and there are many ways that your data can fall into the wrong hands. As well as scanning websites and networks for vulnerabilities and distributing malware, hackers also utilize social engineering tactics such as phishing emails or impersonation. They may also just be opportunists, responding to obvious failures like a laptop left in a pub, or trying out leaked login credentials found online.
Software vulnerabilities
A common way that hackers can gain access to your data is by exploiting a software vulnerability. This includes SQL injection attacks, in which unsecured web forms allow for the execution of database queries, allowing attackers to read and modify the contents of your whole database and potentially gain entry to your network. Cross-site scripting (XSS) attacks are also common — when a hacker adds their own nefarious JavaScript code to someone else’s website, which is in turn run by the victim’s browser, allowing login credentials and other data to be stolen.
Another common software vulnerability is broken access control — allowing people to bypass intended access control through URL tampering, or allowing escalation of privilege (for example, acting as an administrator when only a regular user), or hacking access control tokens to change a user’s permissions. Finally, cryptographic failures are another vulnerability, which can include transmitting plaintext (unencrypted) data, using weak algorithms for cryptography, or having issues with site security certificates.
Poorly configured software
Misconfigurations to your software can leave your infrastructure wide open for a hacker to gain access to your data. For example, not changing your database passwords from the default, or connecting your public-facing infrastructure to your internal network, could allow a hacker to easily get inside your database.
Networks and software configurations need to be hardened against attack. Firewalls must protect all endpoints and be in place at all times, and be configured by an experienced engineer so that no gaps are unintentionally left.
Your software should be up to date, and any infrequently updated plugins or any third-party code libraries or dependencies that you rely on should be regularly checked. These can be an easy source of vulnerabilities that hackers rely on, as they know that many hundreds of organizations often use the same third-party code, so this allows them to target multiple companies at once. Also, they know that most developers overlook third-party code because they didn’t author it themselves.
Other methods
Social engineering: These methods involve deceiving someone into revealing private information or credentials by pretending to be someone else. Hackers may do this by email (phishing attacks), over the phone, or in person.
Lost devices: This happens when an employee takes their laptop, company phone, or USB flash drive out of the office and either loses it or leaves it in an unsafe place where it can be easily stolen.
Stolen or cracked passwords: If an employee reuses their credentials across different accounts, and their password was previously stolen in another breach, this makes it easier to crack their password. Also, if an employee has a weak password, it can be vulnerable to brute force attacks from hackers.
Insider threats: This happens when a rogue employee steals data (often to sell to a competitor).
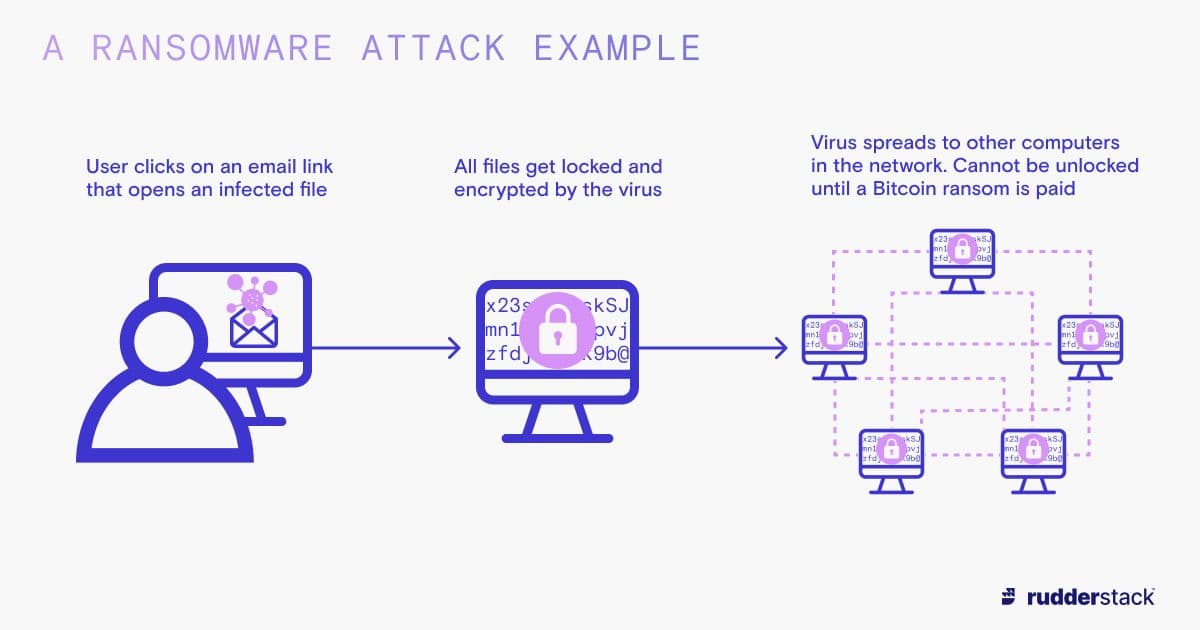
Malware: This can include computer viruses, worms (self-replicating code that spreads to other machines without any human interaction), and ransomware (software that blocks your access to your data until you pay a fee to release it). Never underestimate the ingenuity of the delivery method in a malware attack. Some targeted attacks have been clever enough to involve infected USB flash drives being planted in public places, and even on store counters and workplace desks, just waiting for an unwitting employee to plug them in.
Types of security controls
Physical security controls
Physical security is about protecting the physical places and machines where data is stored, including offices and data centers. Such measures include door access control systems, security badges, and cameras. You should also avoid placing network ports in public areas, which would mean inadvertently granting the general public direct access to your internal network.
Technical security controls
There are many different technical data security controls, including antivirus software (which finds malicious code on computers and quarantines or removes it) or setting up a company virtual private network (VPN), which gives employees a secure way of accessing private networks that are normally only accessible within their physical office. Multi-factor authentication (MFA) is another popular control that forces users to provide extra authentication factors (proofs of identity) besides just their username and password. These are often in the form of a small 4–8-digit code sent to the user’s email address or phone, which they then have to enter into the website. This helps prevent hackers from cracking passwords, as they would also need access to your phone or email account to be able to access your account.
Data encryption is a particularly important security control, as if your data is encrypted, a hacker won’t be able to use it unless they have the encryption key. Encrypt your data even when it’s in transit so that unencrypted data from your users cannot find its way into the wrong hands.
Stay ahead of hackers by installing a firewall, which can monitor all traffic coming into your network and block anything suspicious like a known virus or phishing email. You could also use mobile device management (MDM), which is a way of controlling corporate smartphones and tablets that involves tracking them, enforcing strong passwords and data encryption, and blacklisting unwanted apps.
Administrative security controls
Administrative security controls go hand in hand with technical and physical controls. This includes deciding your data security policies and staff training. Your staff are your first line of defense against things like phishing emails and viruses. With the importance of trustworthy staff in mind, your HR department should also be conducting employee background checks.
Best practices for data security
When reviewing your data security practices and implementing security controls, make sure you cover the best practices detailed below.
Assess your current situation
Start by reviewing your existing data security policies and deciding what extra policies you need. Next, classify your data into different types, such as personally identifiable information (PII) or sensitive data, and decide on procedures for protecting each different category of data.
It’s also a good idea to conduct an asset inventory, particularly of your digital assets such as computers, laptops, and mobile devices, as you can’t protect all the machines in your company if you’re not aware of their existence.
Research vulnerabilities
If you have a company website or web application, check the OWASP Top 10 security risks for web applications and ensure you are protected against them. On top of this, Mitre’s CVE project catalogs all known critical vulnerabilities, allowing you to search for any that may affect your infrastructure. Patch any potential vulnerabilities in your system as soon as possible.
Involve HR
Consult your Human Resources department when implementing your data security controls by having them conduct background checks on all employees. They can also be in charge of ensuring that all onboarding and offboarding procedures have been completed. This includes giving new staff correct permissions, and revoking access when they leave.
When creating new user accounts, enforce strong passwords and multi-factor authentication, and when creating user roles, follow the principle of least privilege (not giving people access to more than they need) when deciding what level of access to give each employee.
HR can also ensure that all staff are trained in security best practices (such as avoiding falling for phishing email scams) by co-ordinating mandatory staff training events or e-learning modules. Ultimately, it’s important that you foster a culture where your staff feel comfortable telling you when they have messed up and clicked a malicious link – you don’t want them hiding this out of embarrassment or fear of reprisal.
Protect your network
A firewall will help keep your company’s infrastructure secure by monitoring all traffic for viruses or other issues. You should also install antivirus and anti-malware software on all machines, and ensure that remote workers can only access your network through a VPN.
Backups
Your data is one of your most valuable resources, so to avoid becoming the victim of a ransomware attack, or losing your data in any other way, back up your data by storing duplicates in multiple different physical locations (such as different data centers). Regular backups make it more likely that if one copy of your data is compromised, other copies remain intact. Storing your data in different locations is also best practice for protecting your data against a natural disaster.
Logging and monitoring
Set up a proper logging and monitoring system for all events relating to data security. Synchronize the clocks on all your systems with a specific time protocol such as the Network Time Protocol, so that if you merge the logs of different systems, they are still readable in time order.
PII masking
PII masking is the practice of modifying PII, such as credit card numbers, to aid privacy or to prevent the risk of theft by an employee or a hacker. This is typically done to data stored in test databases, where some data of roughly the same type and format is needed to test your application but there is no need for real customer data to be stored. Test environments don’t always have the same stringent security controls as production environments, so be careful not to store sensitive customer data in these environments.
Regular audits
Keep your security practices up to date by conducting regular audits of what data needs protecting and the potential threats and vulnerabilities. New software is always being created, which leads to new opportunities for attacks. However, old software that relies on third-party libraries and dependencies that are deprecated or no longer supported can also pose a threat.
Data security controls and customer data platforms
Customer data platforms (CDPs) handle sensitive data, so they should have robust security controls in place, and a certification for a framework such as SOC 2 or ISO 27001 to prove they can be trusted with securing your data.
A good CDP should run on a robust infrastructure that can fail over quickly if there are any hardware or software issues. It should also allow you to retain complete control of any sensitive customer data at all times, so you don’t have to send it to a third party. A standard way to do this is to allow you to self-host the software, or at least to retain full control over the data plane. For additional security of your data, it should also give you options for PII masking of your data before you send it on to third parties.
Further reading
In this article we covered data protection security controls. If you’d like to learn more about data security, take a look at our other learning center articles on this subject.
The Data Maturity Guide
Learn how to build on your existing tools and take the next step on your journey.
Build a data pipeline in less than 5 minutes
Create an accountSee RudderStack in action
Get a personalized demoCollaborate with our community of data engineers
Join Slack Community