Data Security Technologies
Your business will collect data for a variety of purposes, including marketing, managing customer relationships, recording transactions, and maintaining internal processes. Some of this data will be highly specific to your business and a high-value target for theft or electronic ransom. Other data will include sensitive customer information, which is also a target for theft and misuse and is therefore increasingly regulated.
You are responsible for the safety of the data you store. Data loss or a data breach will have consequences that impact both your business’s reputation and its viability, and will incur legal punishment if the required measures to protect customer information were not taken.
This article details the data security technologies that you should be using to protect your data, outlining the purpose and benefit of each technology.
Why is data security important?
The foremost reason many businesses implement or revise their data security practices is to remain compliant with data regulations. Whether a data breach occurs due to accidental disclosure or the malicious action of hackers, regulations such as GDPR, CCPA, and LGPD (among other emerging data regulations for users in other regions) will hold you accountable for any leaked customer data. This can result in hefty fines if you are found to have taken insufficient measures to protect your data.
In addition to these privacy laws, industry-specific regulations like HIPAA, SOX, and PCI stipulate their own data handling and privacy requirements, and may levy additional fines in addition to general privacy regulations. To add to all of this, the customers affected in a data leak may seek their own damages, making the legal ramifications of data breaches incredibly expensive for your business.
Regulatory compliance is not the only reason that you should protect your data. Your customers need to be able to trust you with their data — your business may suffer irreparable damage to its reputation if you disclose your customers’ private information without their permission.
Data security technologies can also ensure the integrity of your data and protect against data loss. Your master data — the core data that your business relies on, like employee and customer records and sales and purchase invoices — as well as the digital materials you use day-to-day are all valuable assets that must be protected. If this data is destroyed or corrupted it will either be difficult and time-consuming to recreate, or be lost forever.
Top data security technologies
The technologies that you implement to safeguard your sensitive and valuable data will depend on the nature of the data, your organizational structure, and the tools and infrastructure you use.
Data identification and classification
 Data Security
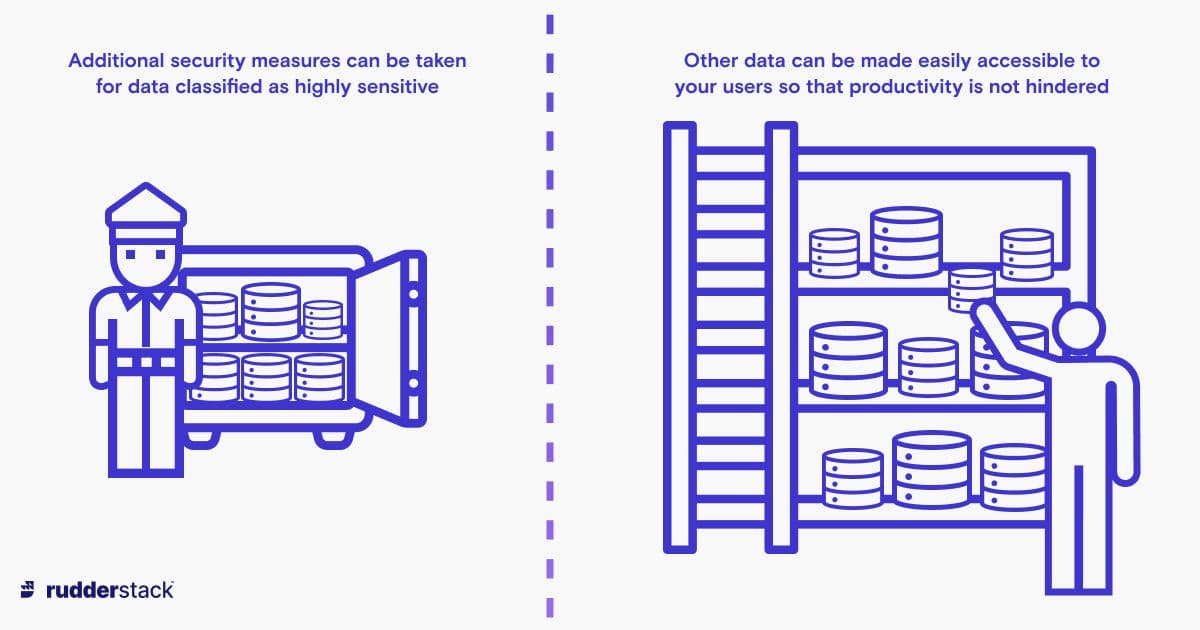
Data SecurityTo protect your data, you must first understand what information you have, so that you can take the appropriate measures. Identifying the data you own and handle on behalf of others means knowing what the data is, where it has come from, and where it is stored. Once you know this, you can classify the data and take appropriate security measures based on the classification of the data.
When classifying data and deciding how it is to be secured, consider the sensitivity of the data, and how readily it needs to be accessed. Highly sensitive data will require more stringent security practices, but this will make it more difficult to access when somebody needs to access it. For example, you may classify your customer records as highly sensitive as they contain personally identifiable information (PII), whereas your product database may not be considered sensitive at all (given that it will be published online through your e-commerce solution).
Data authentication and authorization
Authentication and authorization are the most visible data security technologies. They are the user accounts you use to access your systems, and the permissions granted through them:
- Authentication means verifying that someone trying to access a system is who they say they are. It can consist of a username and password (ideally in combination with multi-factor authentication), or an API key if you are authenticating for programmatic access.
- Once a user is authenticated, authorization checks whether they have permission to view or edit a resource. You can compare an authenticated user’s login with your access policies to find out which resources they are allowed (and not allowed) to access.
You must set up robust authentication methods so that only the people you specify can access your systems and the data they host. Access policies should be regularly reviewed to make sure that they are still up to date — both protecting all of the data they should be, including any newly added or classified data, and granting access to only the people who continue to need it.
When building your access policies, consider again how readily the data you are protecting needs to be accessed so that you do not hinder your employees and encourage them to seek workarounds (like sharing their login credentials with others). For example, you may restrict access to your customer records to your sales agents only so that they can fulfill orders, while your product records can be easily accessed by all staff so that they can update stock levels and add product details without having to seek authorization at every step.
Data encryption
Data encryption is the process of making data unreadable unless you provide the key to decrypt it. By encrypting data, you add another level of protection beyond authorizing access to it — even if it is stolen, it should be unusable without the key to decipher it.
Encrypting sensitive data is considered best practice. However, steps must be taken to secure the decryption key — if you lose it, you lose access to your data. When choosing how you store your keys, decide on an appropriate hardware or software key management solution. Hardware-based key management is more secure, but, like with authorization, if the process of accessing data is frustrating for your employees, they may seek workarounds and share keys or credentials, increasing the chance that they are leaked.
Data can be encrypted both in transit (while it is being transmitted over a network, so that the contents of the data cannot be eavesdropped by intermediate parties), and at rest (on physical storage or while it is in use, so that if it is stolen, it is unreadable).
It is best practice to encrypt your sensitive data in transit using SSL/TLS — as implemented by secure HTTPS and FTPS connections. When storing your data on premises or in the cloud, native encryption for the storage platform should be utilized — this includes EBS encryption for AWS, Oracle Vault for Oracle Database, and BitLocker for Windows Server.
Data masking
Data masking involves altering or redacting data to make it useless if it is stolen. By obfuscating sensitive information that is not needed, you reduce the usefulness of the data to others and thus the appeal of stealing or leaking it and the potential damage done if it is disclosed.
A common example of this is redacting all but the last few digits of a user’s credit card number in customer records — this information is often not required once payment has been made (or it is the responsibility of the payment processor), so masking all of the useful information contained means that your database cannot be the source of a leak leading to fraudulent transactions for your customers.
Data erasure
Under GDPR and other privacy regulations, users have the right to request that the data you hold about them is irretrievably destroyed. You must be able to locate and delete all of the data about that person — whether it persists in your live systems or in archived backups. Data identification plays a big role here — you need to know where your customers' data is stored so that it can be found and updated or removed upon request.
When data is erased, it must be done so in a way that it cannot be recovered — by overwriting it securely, or destroying the medium it is stored on. It is not erased if the data still exists in some retrievable format.
Data backup
Data security isn't just about who has access to your data — it should also cover securing the data itself from loss or corruption. You should keep at least three copies of your data, in separate physical locations. This will protect against hardware failure — as the backups can be restored from a separate device — and against disaster or theft, where the device is physically lost or destroyed. If you are storing data in the cloud, you should keep a copy on a separate platform in case you lose access to your primary provider.
You should make backups regularly, and keep them dated and labeled so that you can readily roll back to a state where you know your data is intact. Attackers may tamper with your data, so having a historical data set to compare with will allow you to confirm its veracity.
Your backups should be treated as being as sensitive as the data they contain, and kept secure. As part of regular testing of your recovery process, the integrity of any encrypted data should be regularly checked to ensure it can be recovered and decrypted.
The people who handle your data
Data protection technologies are not a panacea. Even the best-designed security apparatus is useless if one of your employees just gives the data away (unintentionally or intentionally).
Train your staff to identify potential security problems and flag them up immediately, and ensure that they are aware of common phishing and scamming scenarios. Promote a culture of privacy awareness for your customer data, and responsibility for the valuable in-house data your business relies on.
You should deploy antivirus and anti-malware software on your computers to reduce the number of potential attacks against your employees, but these are never 100% reliable — so make sure your staff are cautious by nature, and that they do not feel like they will be punished for bringing a potential mistake to your attention. It's better to know that a potential security incident has occurred rather than have it covered up.
Data insurance
Some businesses will go as far as to take out insurance on their data, so that if there is a breach of customer data, they are covered for any resulting fines or damages sought and the costs of investigating the cause of the breach.
Insurers will no doubt want proof that you are taking every possible precaution, including implementing industry-standard data security technologies and strategies, before issuing policies (or payouts).
Data security technologies and customer data platforms
Customer data platforms (CDPs) are a secure data solution that provides a unified portal for consuming, transforming, and storing data. They can ingest data from sources including analytics, advertising, e-commerce, and customer relations platforms, as well as your own in-house sources.
When choosing a CDP, ensure that it includes the data security technologies required to protect the data you are handling. Robust authentication and authorization functionality should be present to ensure that your staff only have access to the data they require. Audit logs will allow you to trace problems to the source and monitor for unauthorized access, while data masking can be implemented to make sure that sensitive information is protected. Your CDP should protect the data it processes in transit, and support secure, encrypted storage solutions to ensure the security of your data from ingestion to storage.
Further reading
This article explained the different data security technologies, what they do, and why you need them to protect your business. To find out more about data security, check out the following articles from our knowledge base:
The Data Maturity Guide
Learn how to build on your existing tools and take the next step on your journey.
Build a data pipeline in less than 5 minutes
Create an accountSee RudderStack in action
Get a personalized demoCollaborate with our community of data engineers
Join Slack Community