Data Security Strategies
A data breach can result in serious consequences for your business. You may incur hefty fines, find your reputation has been damaged irreparably, have business secrets stolen, or have vital operational information tampered with or deleted. An effective data protection strategy can help reduce the risk of a possible data breach, keeping your reputation intact and your company running smoothly.
This page will explain what data protection is, and will cover the benefits of having a good data security strategy, as well as describing how you can implement effective enterprise data protection.
What is data protection?
Data protection is the process of protecting your data from theft, deletion or modification by implementing effective data security controls. It is your legal responsibility to protect any personally identifiable information (PII) about your customers or employees, and it’s vital for your business continuity to protect your sensitive trade secrets and other core business data. The data that needs to be protected may be stored in a number of ways, both digital and physical — including data stored in databases, files, user accounts, or even physical filing cabinets.
Why do you need data protection strategies?
Data protection strategies are the measures you use to protect your business from cyberattacks and data breaches. Any breach of customer data will lead to reputational damage to your business that you may not recover from. A data breach can also lead to your company being fined millions of dollars under data protection laws such as the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA), if the authorities determine that you’ve failed to adequately protect your customers’ data. The average cost of a data breach in 2022 was $4.35 million worldwide, and $9.44 million in the US.
Trade secrets and intellectual property are also common targets of cyberattacks. Disclosure or loss of this data could interfere with the proper running of your business or cause a competitor to gain an unfair advantage. Part of an effective data security strategy is backing up your data and storing it in a completely different location, meaning that even if your data does get stolen, you still have access to it yourself – so you can’t be held to ransom over the safe return of your data.
Data breaches are not just caused by external hackers intruding on your network. Breaches are frequently caused by internal factors such as poor enterprise data protection policies and procedures. Sometimes internal breaches happen intentionally, when an employee leaks data for personal gain, but often they happen when an employee leaks data by accident or without thinking. An effective data security strategy will help ensure your staff are trained to understand how they can prevent such breaches.
How to develop an effective data security strategy
Before you start working on your new data security strategy, it’s worthwhile to do some research on the main areas your strategy should cover, as well as deciding on a good order in which to cover all the steps in your process. You should start by looking at what data you currently hold, and also assess any existing data protection strategies that are in place.
Data risk assessment
Identify the data you need to protect, including the type of data it is, how sensitive it is and how long you are holding it for. You can classify whether the data is public, private, or only accessible to certain groups of people. This will inform your next task, which is to work out which data protection laws you need to be compliant with. Once you have this information, it can inform what your data security strategy may need to cover.
Auditing your existing data security strategy
Conduct an assessment of your existing data security approach, documenting any weaknesses and vulnerabilities. You can then order your vulnerabilities by urgency and complexity to help prioritize which should be fixed first. As part of your assessment, make a note of all the versions of any software that you’re using, including any known vulnerabilities with these versions. It’s best practice to be running the latest version of all software that connects to your network, so you can use this list to help you upgrade. Serious vulnerabilities must be patched, and legacy software should be disconnected or isolated from the rest of your infrastructure. You should now be aware of any main gaps between your existing data security strategy and what needs to be covered, and these are the areas you will need to develop policies and procedures for.
Policies and procedures
You are now at a stage where you are ready to decide policies and procedures. You should consider policies for the following:
- Role-based access control: This is a type of data access control where you assign roles to staff and teams, and decide which roles should have access to what data. You should apply the principle of least privilege when deciding what roles to assign to staff. This principle states that people should only be given the level of access needed to do their job and nothing more. One way to ensure this is to have many granular levels of different roles, rather than only a handful of different roles that give many different privileges at once. The principle of least privilege applies to both staff within your company and third parties who have access to data.
- Network firewall: This should be used to inspect traffic and block any unauthorized access to data.
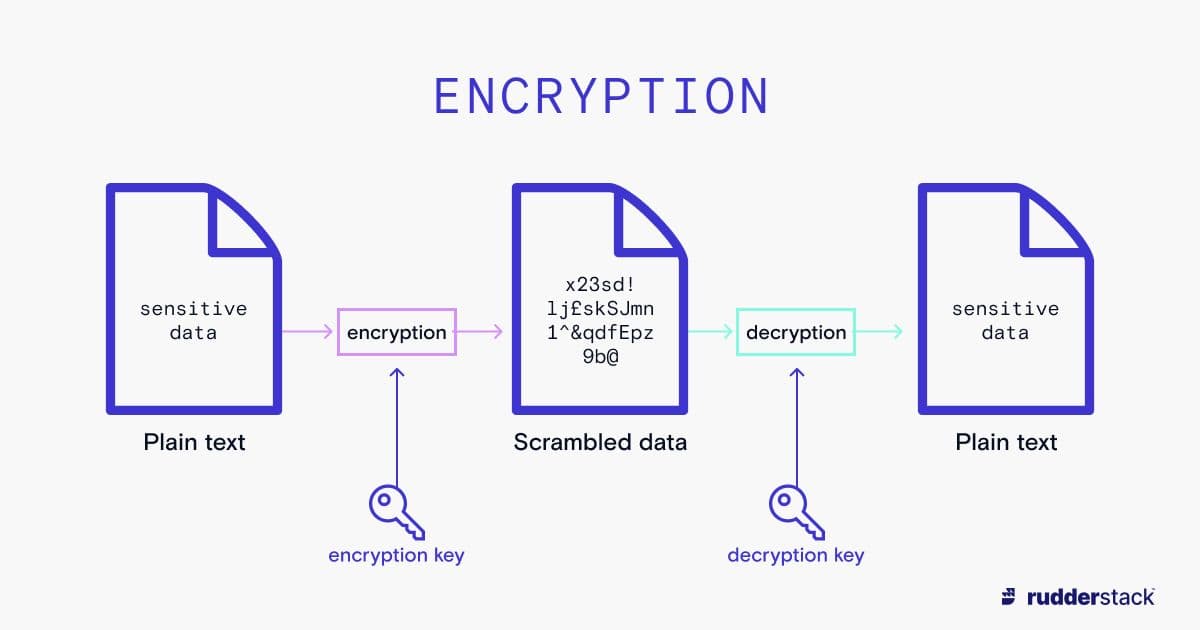 Encryption
Encryption- Data encryption: Sensitive data (such as PII) should be encrypted when sent over a network or stored with a third party so that if it is leaked, it is unreadable. It’s important not to lose your encryption keys as there is no way of decrypting the data without them. Keys can be safely stored in a secrets management tool such a Vault or AWS Key Management Service, or you can even burn the keys to a read-only CD (or print them out) and store them in a physical safety deposit box.
- Antivirus software: Install antivirus software on all company devices, including mobile phones. Antivirus software is useful for protecting individual devices; however, if you also need to protect networked machines from cyberattacks, you will need to install endpoint protection software on your network. This software allows you to manage security software for all devices from a single management dashboard instead of having to manually install protective software on all machines.
- Enforce multi-factor authentication (MFA): MFA forces users to provide additional proof of identity beyond their username and password when logging into your site or app. For example, they may be required to prove that they have access to their mobile phone or email account. This can be checked by getting the system to send a short code to the user via SMS or email. The user then usually has around 30 seconds or a minute to type that code into the website, thereby verifying that they have access to the phone or email account.
Staff training
Staff training is a crucial part of any data security strategy. You shouldn’t rely on antivirus software as a technical panacea – your staff need to be made aware of the social engineering methods that hackers can use to try to gain unauthorized access to your data, and trained to spot potential scams and suspicious downloads and attachments. Scams can include phishing attacks, compromised software installers and other files downloaded from the internet, impersonating an employee over the phone or in person, or leaving infected USB sticks where your employees are likely to find them and plug them into company computers. Your staff should also be made aware of the risks of taking company devices off site, and know how to keep them secure.
Your software developers should never hard-code passwords or other secrets in any source code or configuration files that could be stored in source control, as source control is often hosted externally (outside of your control), and data breaches do happen. Even though software developers are more likely than the average employee to have a good awareness of data security, in practice these precautions often need to be reiterated.
It’s important to foster a culture of responsibility where every member of staff understands that they are collectively responsible for data security. However, you’ll want to ensure that staff don’t feel intimidated into staying silent when they have made a mistake that may have led to a data disclosure. If they feel comfortable admitting their mistake, it can be addressed early, maybe even before the mistake has a chance to result in disclosure, or at least it will give you the chance to minimize the damage.
Physical security
Despite the focus on cybersecurity in the age of cloud computing, computers are always ultimately stored in a physical location, and network access is available to any employees who work in a physical office. Physical security is just as important as it always was, and goes hand-in-hand with any cybersecurity practices, so you should conduct a review of the effectiveness of your physical security. This could include cameras, security guards, and locks. You should also consider whether the places you store data are well protected against fire, flood, and natural disasters. Segmenting your data so that it is stored across multiple physical locations is a good practice, and this is an option that many cloud providers offer.
Backup and recovery
Ensure that you’re backing up your data and that you regularly test your ability to recover data from a backup. This can help to render a ransomware attack useless, as your data can’t be held to ransom if you have another copy of it. You should back up your data at least daily, and ideally a lot more often than that if your data is actively changing throughout the day. Ensure you add a timestamp to each backup so it can be identified.
Data masking
If you need to create copies of a database that will be hosted on a less secure staging or testing server, ensure that any PII is masked. Data masking is a way of replacing your data with similar data so that it can still be useful in testing scenarios but so that it is no longer real-world data.
Data erasure
Data privacy laws such as GDPR give customers the right to request that their data be amended or deleted. If you have a good customer data management strategy in place, you’ll be able to track user data across your infrastructure, so if a request comes in to remove it, all the data can be found and removed. However, simply deleting this data does not mean it can’t be recovered. You will want to also perform data erasure, which overwrites the whole file system after deletion, meaning the data can never be recovered.
Regular monitoring of your data security strategy
Conduct an annual review to ensure that you are still following best practices for your data security strategy. Also, if you add new software or methods of data storage to your stack, you will need to check that the data stored in them is protected. Keep things simple by focusing on a streamlined secure toolchain — the less the parts move, the less can go wrong.
Customer data platforms (CDPs) and data security strategies
Data security is fundamentally important to your business. Data breaches can cost you serious amounts of money in fines and reputational damage, and can also cause disruption to the smooth running of your company. Investing in a data security strategy before a breach is the smart thing to do. Consider how you could improve the policies and procedures in your company, as well as the technical solutions that help you with data security. If you do this alongside auditing your existing strategy, you will be in a good place to implement your new data security strategy.
When choosing a customer data platform, it is worth checking that they have a good reputation for data security, and that they have been certified as being compliant with a major cybersecurity framework such as SOC 2 or ISO 27001. When outsourcing any data to a third party, it’s important to check that their data security is at least as good as yours, and certification is an easy way for them to prove that they take their data protection seriously.
In this article we’ve covered data protection strategies. To continue learning about data security, check out these other articles from our learning center:
The Data Maturity Guide
Learn how to build on your existing tools and take the next step on your journey.
Build a data pipeline in less than 5 minutes
Create an accountSee RudderStack in action
Get a personalized demoCollaborate with our community of data engineers
Join Slack Community