Cybersecurity Frameworks
Introduction
As remote work and cloud infrastructure become increasingly common, cybersecurity is becoming even more important for good business practice than physical security. Cyberattacks can steal sensitive data, take control of computer systems, or lock companies out of their data and hold it for ransom. Loss of sensitive customer data can have drastic consequences for your business in terms of reputational damage and financial penalties; compromised operational data can dull your business’ market edge.
Following a cybersecurity framework will help protect your organization against cyberattacks. Some cybersecurity frameworks allow your company to be certified by an external auditor, and this can act as proof that your company is in compliance with government legislation. For example, certification in the HITRUST cybersecurity framework is proof of compliance with HIPAA, and having a comprehensive certification such as ISO 27001 can be taken as proof of compliance with many types of data protection legislation such as GDPR, CCPA or LGPD.
This article covers the types of cybersecurity threats that you may face, and assesses how companies can protect themselves against cyberattacks using a range of cybersecurity frameworks. The most popular frameworks are compared and contrasted, helping you choose which framework is most suited to your particular business case.
What is cybersecurity?
Cybersecurity is the practice of protecting your electronic data and critical IT infrastructure from being accessed by criminals or unauthorized persons, and of stopping them from modifying or deleting your data. Cybersecurity is also known as IT security or computer security; the terms are interchangeable. However it is slightly different from a similar-sounding term, “information security”. Information security protects all your data (both electronic and physical), whereas cybersecurity is a particular subset of information security that is only concerned with protecting digital data.
Types of cybersecurity threats
There are a huge number of ways that hackers might gain access to your data or critical infrastructure. Here is an outline of just a few of these ways to show the variety of different methods that need to be prevented.
Malware: This is software that attacks a computer system for nefarious purposes. Criminals find many ways to get malware onto a computer. They might exploit a software vulnerability, or convince a victim to click an email link that installs the software on their machine.
Man-in-the-middle attacks: These happen when hackers insert themselves in between two systems that communicate directly with each other, either to eavesdrop or to intercept and alter the information.
Social engineering: This is an umbrella term used to describe methods of gaining access to digital assets by manipulating people into giving out restricted information or by getting them to unknowingly help with the cyberattack in some other way. When it comes to corporate cybersecurity, the people being manipulated are generally employees. A well-known example of social engineering is phishing emails: scam emails that pretend to be from someone reputable to gain personal information or trade secrets. Another example is baiting, which could involve tailgating behind a real employee through a security-controlled office door, then leaving an infected USB flash drive lying around, with the hope that an employee will find it and insert it into a network computer out of curiosity.
Password attacks: A hacker may create simple scripts to help them with cracking a user’s password. If you reuse the same password regularly and this password was leaked in a previous data breach then you are an easy target. Short or weak passwords are also at risk from brute force attacks.
SQL injection: If your web forms don’t sanitize input from users, they may be able to run SQL queries on your production databases, thereby viewing or modifying sensitive information.
Cross-site scripting (XSS): In the case of XSS, hackers send their victim an email containing a malicious link. When the user clicks the link, it takes them to your website, but also adds the hacker’s nefarious code to the page they load. From the victim’s perspective they are using a trusted website, but if they log in to your website or submit information on a form, the hacker’s code can steal this private information.
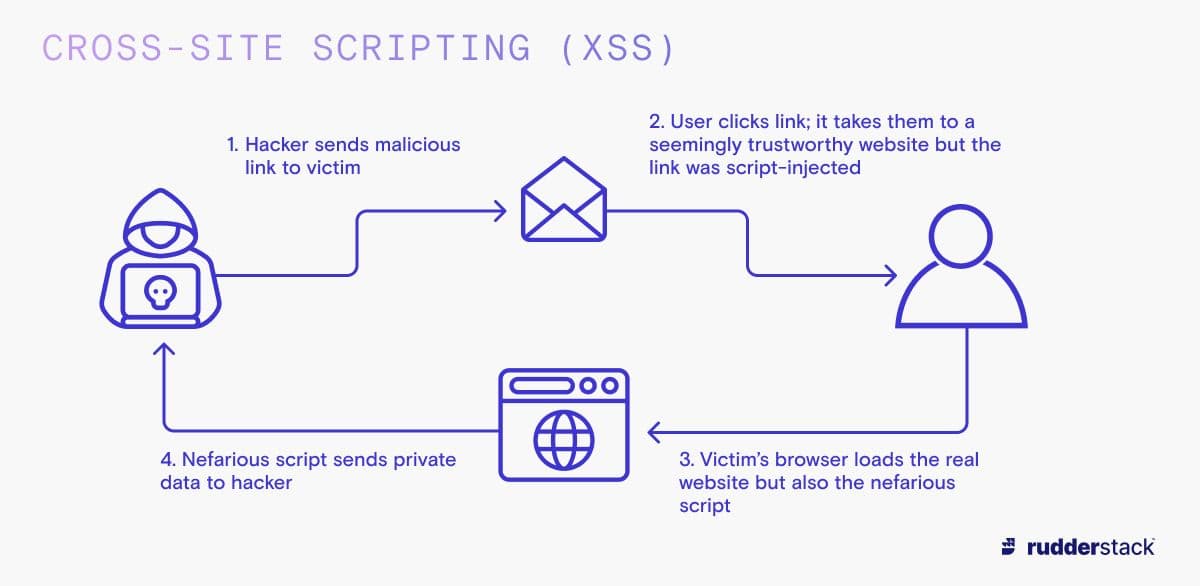 Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS)Distributed denial of service (DDoS): This is a coordinated attack where so many users visit a website at the same time that the system becomes overwhelmed and shuts down. A DDoS attack is not done to gain access to data — it is more about causing disruption to companies and stopping them from being able to control their own systems. It might not seem like as much of a threat as having your data stolen — but if you run a company with a web-based product, you do not want unnecessary downtime! These kinds of attacks are on the rise. A survey by Kaspersky of over 5500 companies found that over 20% of larger companies reported that they have been the victim of at least one DDoS attack.
What is a cybersecurity framework?
A cybersecurity framework (or IT security framework) is a system of best practices for having effective cybersecurity within your organization. These frameworks are not legally binding in and of themselves, but following a top cybersecurity framework will help you comply with legislation and prove this compliance to your customers.
Why are cybersecurity frameworks important?
A cybersecurity risk management strategy is important because it protects your data from theft or modification, which is necessary to maintain your customers’ privacy and your company’s reputation. If you follow a high-quality cybersecurity framework, it will help you avoid hefty fines from regulators and stolen business secrets. Cybersecurity is becoming a more complex field: you can’t just pay for some antivirus software or a firewall and hope for the best; nowadays you need a much more comprehensive data security strategy.
Following a cybersecurity framework gives you the confidence that all the main bases are covered in terms of IT risk analysis and cybersecurity. On top of this, it’s becoming increasingly common for clients and partners to insist that you're following a specific cybersecurity framework, and as it can take many months to become certified, it’s best to start the process before it’s demanded. Investors are also starting to focus on cybersecurity as part of their screening processes, so if you’re seeking investment funds you’ll want to present evidence of a strong framework in your presentations.
As well as ensuring that your systems are in compliance with a cybersecurity framework, you should also consider how secure potential vendors are when purchasing new software products. Many data breaches happen because companies use software dependencies that are not secure. It’s important that any companies you work with have a certification from a reputable cybersecurity framework, as a data breach at a third-party vendor can put your company at risk.
Top cybersecurity frameworks
Different cybersecurity frameworks are best suited to different use cases. For example, some are best if you are working in a specific industry, or if your organization is a particular size. We’ve drawn up a comparison of the best and most common frameworks, along with details of the ideal use case for a particular framework and the benefits of implementing each.
ISO 27001
The International Organization for Standardization (ISO) is the oldest standards organization in the world, and is the gold standard for judging cybersecurity. The ISO 27001 framework is a framework for information security management, of which cybersecurity is a big part. Your organization can be assessed by an external auditor and become ISO 27001 accredited, or you can choose the cheaper option of certifying just one of your products as being ISO 27001 compliant. ISO 27001 is very comprehensive, but is expensive to implement, so you have to decide if you have the time and resources to commit to it.
SOC 2
SOC 2 is a common framework used by software-as-a-service (SaaS) companies. It is a trust-based cybersecurity framework that allows you to use more relaxed forms of access control when working with third-party vendors as long as you both have SOC 2 certification. Being SOC 2 certified means both parties can trust each other and can therefore transfer data between the different companies’ systems with less stringent access control requirements. This framework generally costs less to implement than ISO 27001 as its scope is strictly cybersecurity.
NIST Cybersecurity Framework
The NIST framework was developed by the US government, initially for its own use. It’s now widely used in professional and governmental organizations. NIST is a voluntary framework, so it does not offer official certification. However, if you are a US federal government agency, you must prove you are compliant with FISMA regulations, and following NIST is necessary to do this. Non-FISMA compliance will lead to a loss of government funding for your agency.
Companies following the NIST framework have to compare themselves to a profile of an ideal organization, identify where the gaps are, and then develop a roadmap for where they need to go to achieve their goals. Organizations do this by ranking themselves on 5 core NIST functions: identify, protect, detect, respond, and recover. NIST has grown in popularity and now many industry-specific frameworks are based on NIST, such as the TSS Cybersecurity Framework, which is the transport sector’s version of NIST that focuses on transport and critical infrastructure.
CIS Critical Security Controls
The CIS Critical Security Controls is a simple list of 18 action points that will help you deal with the most common cybersecurity risks. Like NIST, there are no external auditors — it’s just a framework to which organizations can standardize themselves. The different action points have a lot of overlap with other big cybersecurity frameworks, so if you are newly introducing a cybersecurity framework, it’s a great idea to start with some of the CIS security controls while you’re evaluating whether you want to pay to be compliant with one of the larger frameworks.
HITRUST Cybersecurity Framework
HITRUST is a healthcare-specific cybersecurity framework. Having a HITRUST certification proves that you’re compliant with HIPAA regulations, which is a legal requirement when working with US healthcare data. Depending on the type of assessment you get from HITRUST, this can also include a report on how compliant you are with NIST as well. You should adopt this if you are a US government agency or private business and deal with sensitive US healthcare data.
Cloud Security Alliance’s (CSA) Cloud Controls Matrix (CCM)
The CSA CCM is a framework of 197 control objectives spread across 17 different domains within cybersecurity, specifically related to cloud computing. You can be added to the CSA Star Registry if you’re in compliance with their framework. There are different levels for this; level 1 is the simplest and involves a self-assessment, whereas level 2 involves a third-party audit. Level 2 is considered a cloud-computing-specific extension if you already have either ISO 27001 or SOC 2.
Payment Card Industry Data Security Standard (PCI DSS)
The PCI DSS was created for the payment card industry, and is now mandatory for any company that processes credit card data. It focuses on payment security processes and payment-specific aspects such as safeguarding and restricting access to cardholder data.
| Framework | Ideal use case | Suitable organization size | Relevant regions | Difficulty and cost to achieve | Benefits and reasons to implement |
|---|---|---|---|---|---|
| ISO 27001 | Large organization with money and resources | Medium or large | Anywhere | High | Internationally recognized Integrates well with ISO 9001 (due to shared policies) Covers all areas of information security It is the gold standard internationally so sometimes clients insist on it |
| SOC 2 | SaaS company | Any | Anywhere | Medium | Cheaper and easier to implement than ISO 270001 as the focus is just on cybersecurity Still has a great reputation internationally |
| NIST Cybersecurity Framework | US government agency (NIST is compulsory for these) | Any | USA | Low | Ensures compliance with FISMA, which is mandatory for US federal agencies |
| CIS Critical Security Controls | Small business | Any | Anywhere | Low | Easy to understand and get started Compliant with other more comprehensive standards like ISO, PCI DSS, and HIPAA, so it’s easy to switch to other standards when you’re ready |
| HITRUST Cybersecurity Framework | Company that processes US medical data | Any | USA (or anywhere processing US medical records) | High | Proves you’re in compliance with HIPAA, which is mandatory if you work with US medical data |
| CSA CCM | Company with data stored in the cloud | Any | Anywhere | Medium | Focuses on security best practices in the cloud only Can be awarded as an extension of ISO 27001 or SOC 2, or there are lower levels such as self-certification |
| PCI DSS | Company that processes payments | Any | Anywhere | High | The gold standard for proving to payment companies that you are trustworthy Mandatory if your company processes payments |
Conclusion
Many cybersecurity frameworks have overlaps and some target a specific industry or area. Sometimes the framework you will need will be dictated by your clients; for example, it’s common for big companies to demand you’re ISO 27001 or SOC 2 compliant. If you are working on a US government contract, you may need to use the NIST framework.
If you have the freedom to decide for yourself, cost may be the biggest factor. If your company is struggling to agree on a framework (or budget!), you can start by following the free advice of CIS Critical Security Controls while you deliberate on which level frameworks you want to pay for.
As well as being concerned with which cybersecurity framework you should be following, part of having a really comprehensive cybersecurity strategy means evaluating how safe your data will be if you’re considering allowing third parties to share your data. It’s important to check that any partners or third parties are following cybersecurity best practices, and if they are certified as being compliant with an appropriate cybersecurity framework, this can give you confidence that they are safe to work with.
Further reading
In this article we compared different cybersecurity frameworks. If you’d like to find out more about cybersecurity and related subjects, take a look at our other learning center articles.
The Data Maturity Guide
Learn how to build on your existing tools and take the next step on your journey.
Build a data pipeline in less than 5 minutes
Create an accountSee RudderStack in action
Get a personalized demoCollaborate with our community of data engineers
Join Slack Community